Today when looking to download a new version of VLC Player, I got served with this malicious advertisement on google and thought it might be an excellent opportunity to show how to make a quick malware triage. In this article, I show not only what are the dangers of malicious advertisements in google, but also how to triage malware in 30 minutes without any knowledge of coding, assembly, or reverse engineering tools like disassemblers or debuggers. I only use basic, freely available tools but yet I am able to discover not only malware family, and all important indicators of compromise (IoCs) but also can make good assumptions about its capabilities.
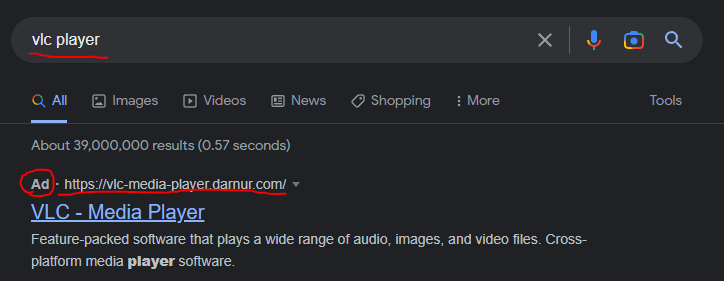
When seeing this ad, I instantly knew it is gonna be malware. This domain looks very suspicious and this displaying as an ad, but not in the top search is a very strong indicator that it is malicious. This is a so-called malvertising technique, and it is recently becoming a more and more popular way to spread commodity malware.
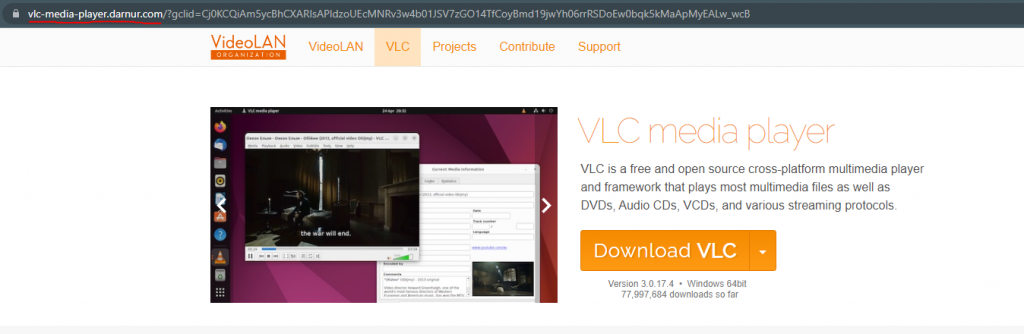
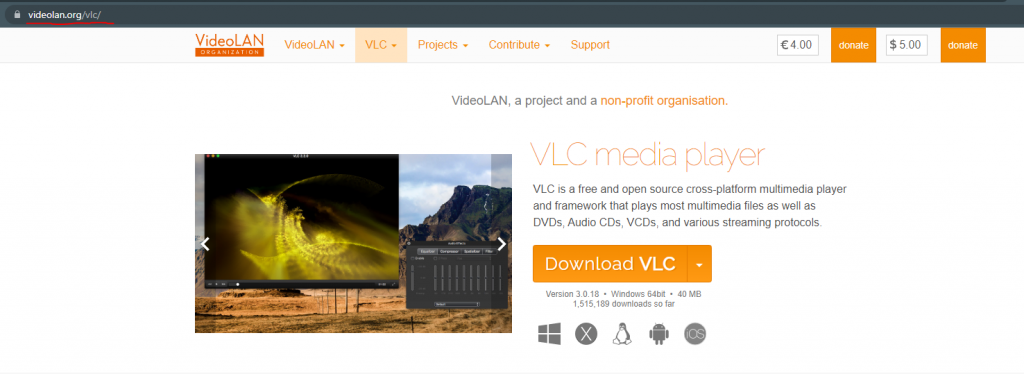
When we click on the malicious ad, we can clearly see that the website was quite well cloned from the official videolan website. In the above pictures, you can see the similarities. What is interesting, there are some differences too. For example, fake VLC has 70 million downloads, while the real one has only 1,5 million.
If we click on “Download VLC” it will download a SoftwareSetupFile.zip (sha256: B43BD295397F315BC897900FF892BBB9EAFD4E4B5D608443451E37D554934C0E) that contains Setup.exe (SHA256: 9CB1F2B183CA9D483D6FCA28A307D39EF9BE3A802CFC6C94E543C62E8DEBD67C).
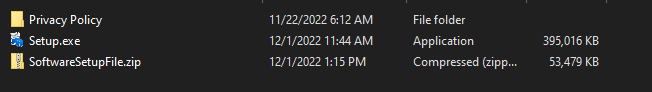
As we can see Setup.exe is almost 400MB in size. This is a clever trick used by malware authors, called field bloating and its purpose is to avoid automatic scanning with sandboxes and scanners that have a size limit. There is a cool blogpost by Tony Lambert on how to remove these additional bytes if you want to use a sandbox that has a size limit. In our case, we take a different approach. At first let’s upload it to VirusTotal:
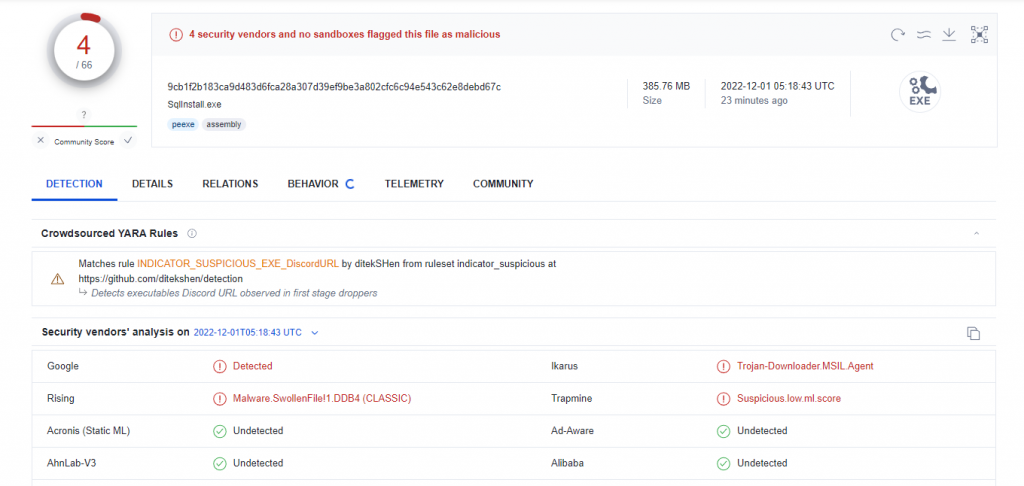
As we can see file detection rate is not that good but we can already see something is not right here. Let’s have some fun and run this sample in our analysis environment.
Before you execute malware, watch my video on how to setup a safe analysis environment first!
Before we run our sample we make sure to launch a few analysis tools. Tools I usually use are Process Hacker, Process Monitor to monitor process behavior, and Fiddler with my own proxy to monitor network behavior. I also use Burp + Inetsim to simulate internet connections.
After executing a binary in our VM, we can see a fake installation button, that is not very convincing. When we click on it, another window pops up.
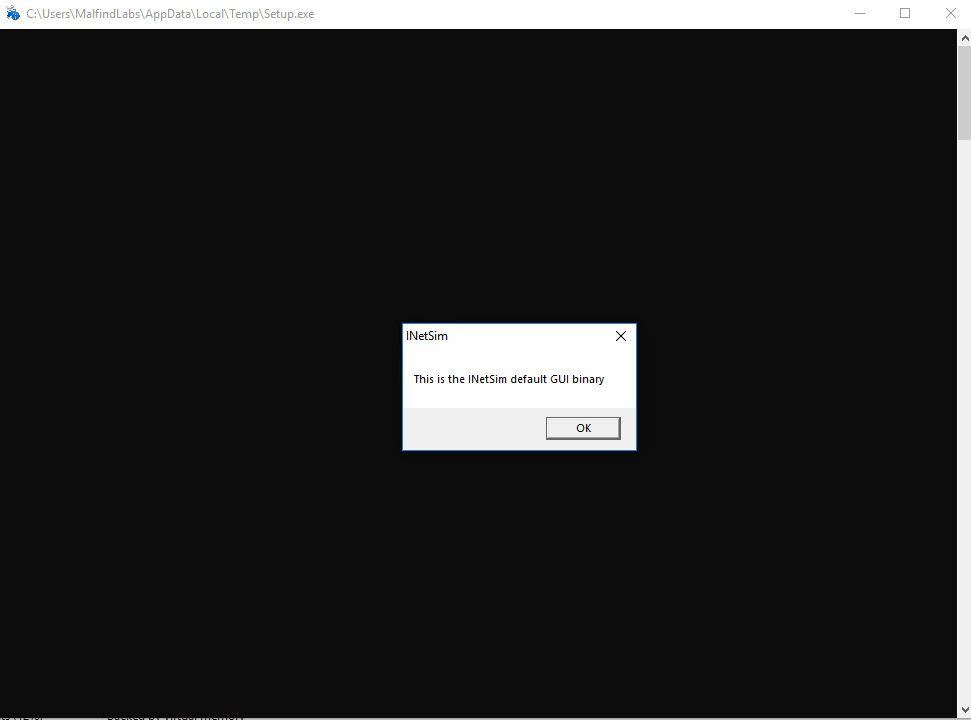
This is not what the actual victim would see but a default binary from INetSim that’s getting executed. Since we are in the simulated environment, this means something tried to download some executable from the internet, and INetSim served a dummy binary instead, that later got executed. Let’s see what’s going on in our network connections then.
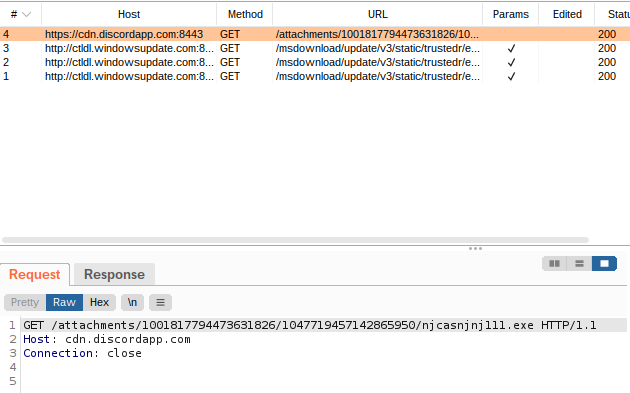
It seems there are some connections to Discord CDN. This might look legitimate at first but don’t be fooled! CDNs and especially Discord CDN are popular places for malware authors to host their payloads. It looks like legitimate traffic, and CDN domains are often whitelisted in the proxy environment. We can see it tries to download some executable file from there, this is probably what it tried to execute, but INetSim served a dummy executable instead. Let’s download it ourselves and see what is it hiding.

We download njcasnjnj111.exe (SHA256: 77648473A36693CE3547880CB361F10ED937F0D43839CAD51DE7C8D4AC9709B8) using wget on linux. Before we execute it, let’s see what VirusTotal thinks about it
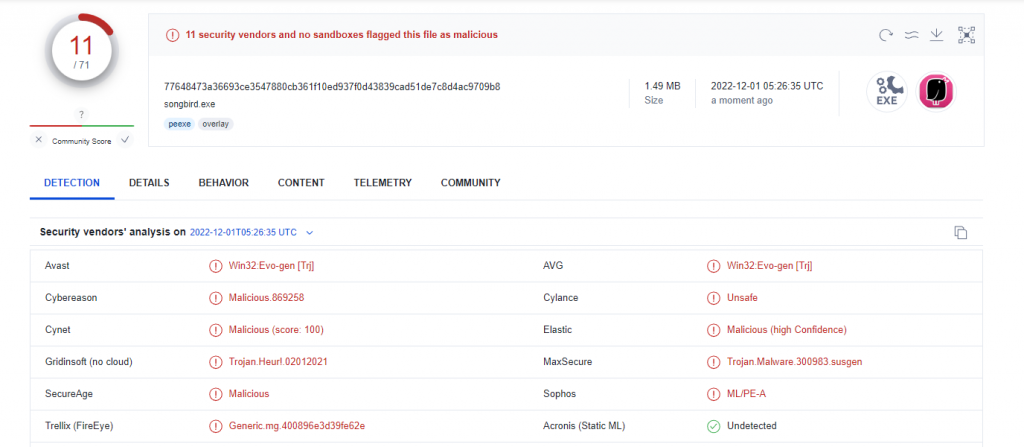
Slightly better detection rate but it’s still far from perfect. We can clearly see it is malicious though. Let’s execute this binary in our analysis environment using same tools

Not much happens at the first sight, it launches a copy of itself that is suspended for some reason. It is also listed as Songbird Web Player for some reason. Let’s look at the network connections first, using Fiddler for change.
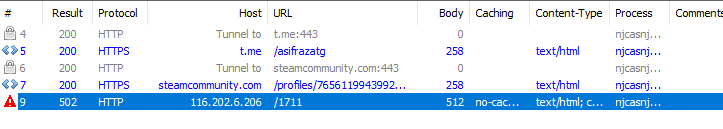
There are a few interesting connections here. The first one is to a telegram site, the second one is to a steam community profile and the third one is directly to an IP. We can verify the first two links and see they contain different IP addresses. We can safely assume this is a special C2 (Command and Control) server update mechanism, so the third IP address will be, most likely, a default C2 address.
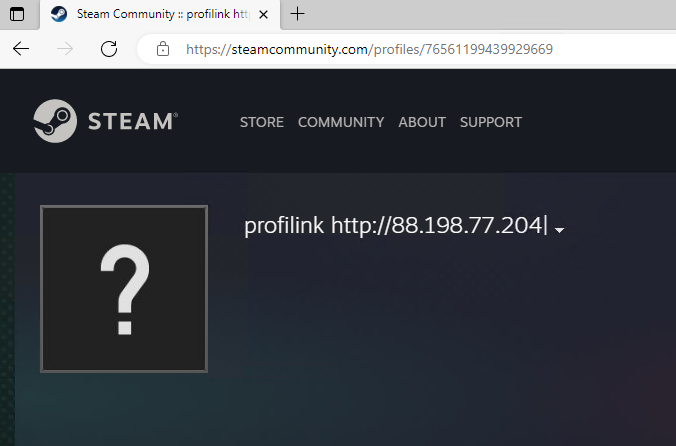
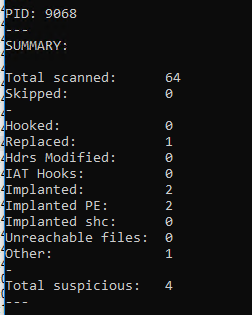
We already have a C2 server, let’s now try to dive a little bit deeper and guess the malware family and its capabilities. One thing we can do without using advanced analysis methods like debugging is to try to automatically unpack the sample, which will allow us to understand it better. I wholeheartedly recommend https://unpac.me/ for unpacking but this time we will use PE-Sieve by Hasherezade. We just point it to the proper PID and hopefully, it will do everything for us:
It seems it unpacked 4 suspicious memory regions but really only one file will be of interest to us.

We can see it dumped a specific executable: 4e70000.njcasnjnj111.exe (SHA256: 582C4ACBC092B21873D8783FD598434D4699FFD5727C193565CF6A123BF34D28). Let’s see if there’s a difference if we upload it to VirusTotal
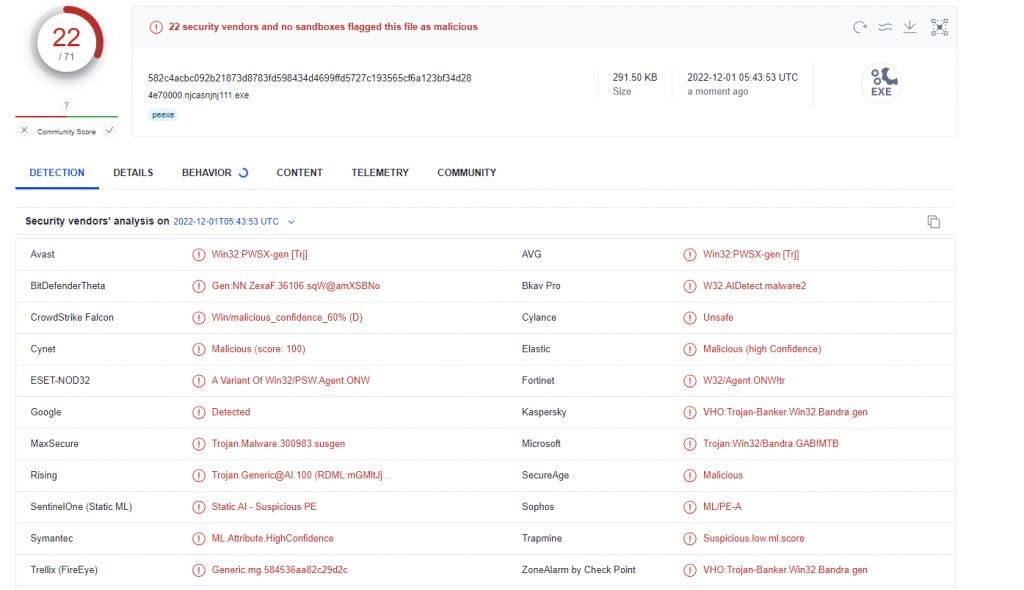
As we can see, much more Antivirus engines detect a dumped process, although it is still far from perfect. Some signatures also try to hint at the family, but AV signatures are not very reliable for this kind of attribution, so better not to trust them. Sometimes we can get lucky and our sample matches some community Yara rules, they are usually much more reliable in detecting a malware family. Another thing we can look at, are community comments, they are mostly from automated scanners and are usually reliable too, but appear only after some time (when the scanner discovers a new sample). In fact, there was a comment with the correct malware family appearing on this upload but I won’t spoil it for now.
We will take a slightly different approach to see what other tools we can use to identify a malware family. There are a few good free online sandboxes out there, that can actually do great work triaging malware for us. I didn’t want to use them initially in this post, as I wanted to show you how can you triage the malware manually (and usually it is better to upload unpacked samples, especially for family identification and static signatures). But for family identification there are usually not much better options, unless you are a seasoned malware analyst that can recognize different malware families just based on their code patterns or behavior. Sandboxes usually have a set of specific signatures both static, and behavioral to detect malware families. One of the sandboxes I like to use is Intezer Analyze, due to their specific approach to attribute not an entire sample of malware to one family, but specific chunks of code. This makes sense as many of malwares are actually just code from other malware patched together. The basic functionality of Intezer Analyze is free, but be careful – your sample will be available publicly, so don’t upload anything confidential (the same goes for every public sandbox). After uploading our sample, Intezer will try to match its code to different known code samples, and make a match.
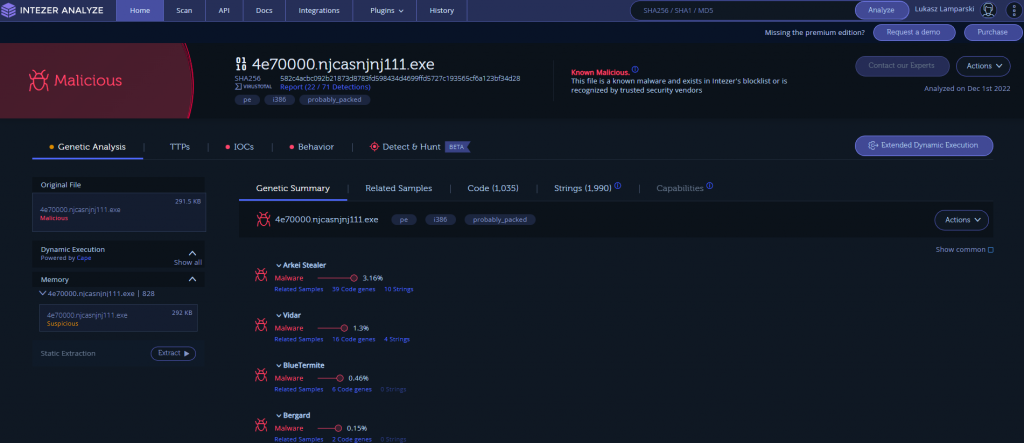
Unfortunately, results here are also inconsistent – we have some matches but only a few percent of the code actually matches something, which is not a good indicator. We can make a note of detected malware families though, the top 2 ones are Arkei Stealer (3.16%) and Vidar (1.3%). If we read some articles about Vidar, we would know it is actually based on Arkei, so this is already some clue. We can also check some interesting strings in there (see anything familiar in there) and which code patterns match which malware.
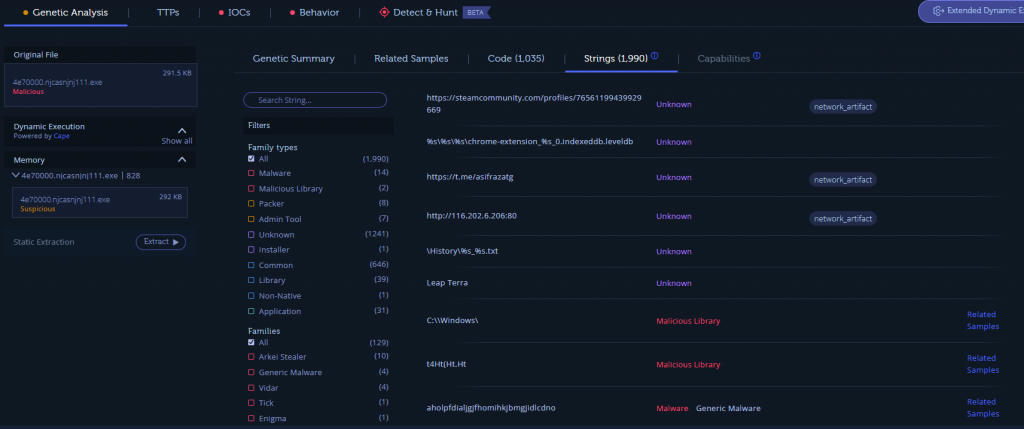
Another useful sandbox is Hatching Triage – I often use it for fast wins. We can upload our sample there, and it will run it on different virtual machines, trying to find not only behavioral patterns but also a malware family.
As we can see, Triage is quite confident this sample is Vidar. This is quite consistent with what we’ve seen from Intezer, although there seems to be more confidence here.

Triage was also able to extract an exact malware config, including not only family but also version and botnet number. This gives us even more confidence, the classification as Vidar is correct. Config extractors used by sandboxes are usually family-specific, and if sandbox would misjudge the malware family, it would not be able to extract the config.
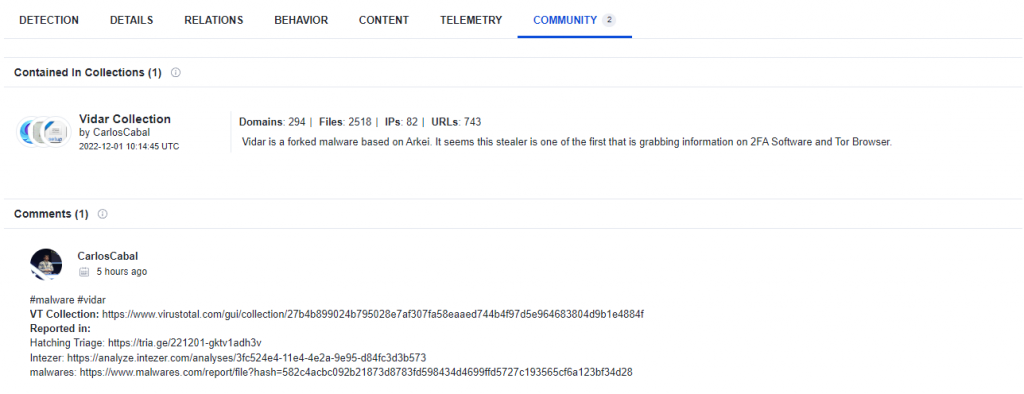
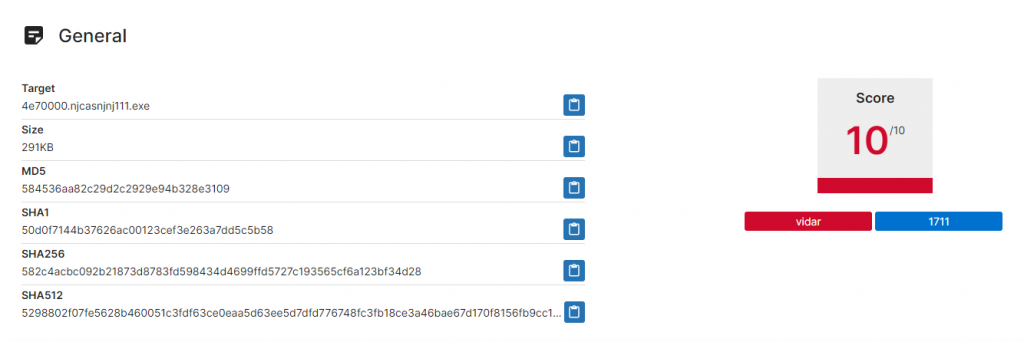
For final confirmation, if we go back to our VirusTotal submission, we can see this was added to Vidar Collection and marked as Vidar by some automatic community scan. Right now we can have 95% confidence we got the family right. You can read more about Vidar on malpedia.
Ok so we have C2, we have malware family, what can we do more? What if we want to know the exact capabilities of this malware? This usually requires a deeper investigation and lots of reverse engineering to understand the code of the sample. But what if I tell you there are some quick wins you can get even in this department?
The first great tool we can use is Capa from Mandiant. It scans a code and looks for code patterns to discover the behavioral capabilities of the executable (not only malware). It won’t tell us exactly what the malware’s goal is, but it will tell us what can is it capable of doing.
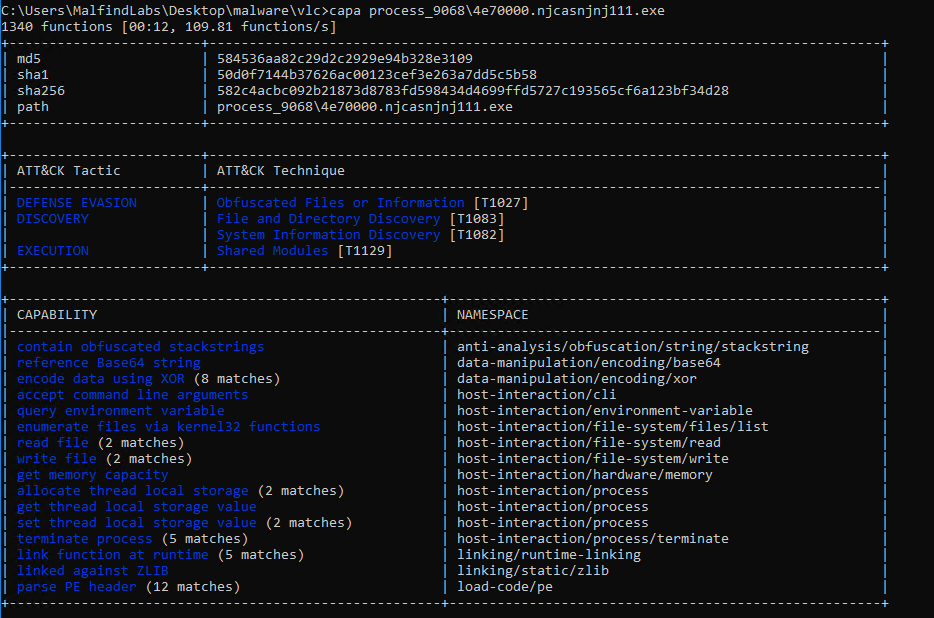
In this case, we can see file can read and write files, it can encrypt data using XOR as well as it has ZLIB included as a linked library. It can already give us some clue as to the type of malware, but not much in this case. There seem to be some obfuscated strings involved, so maybe there is an easy option to see what is hidden there.
What lots of malware does is hide/obfuscate its most important strings when lying dormant on the disc, and only deobfuscate or decrypt them when running in the memory of the infected host. That’s why static analysis won’t reveal much about such malware. Fortunately, we have tools like Process Hacker, that will not only allow us to see the live memory of the running process but also dump it to the disk.
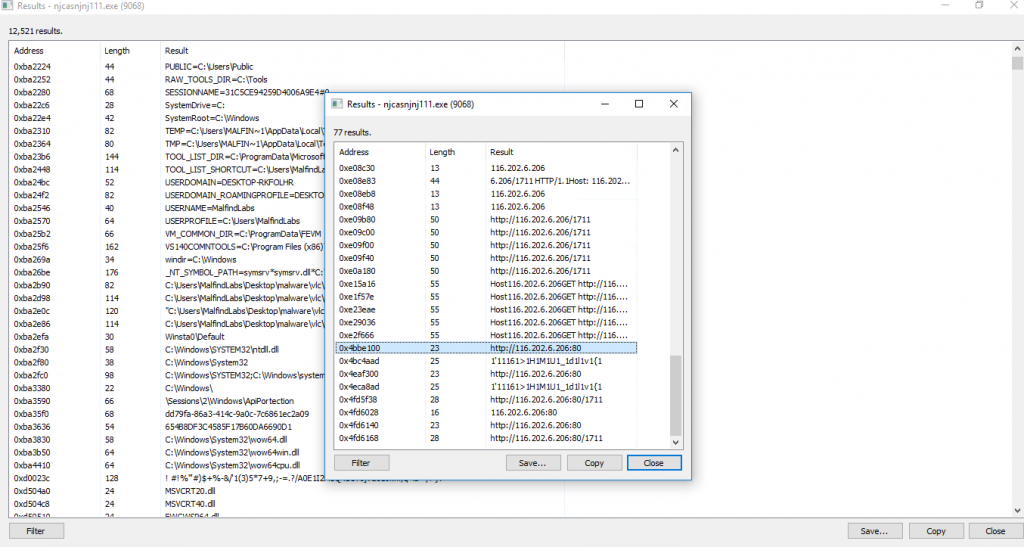
As we can see process hacker allows us to inspect strings in the memory, and we can already have some quick wins, and for example, find our C2 address. But for deeper analysis of memory-resident strings, it is usually better to dump process memory to the disk and analyze it there. For this we can use dump option of process hacker.
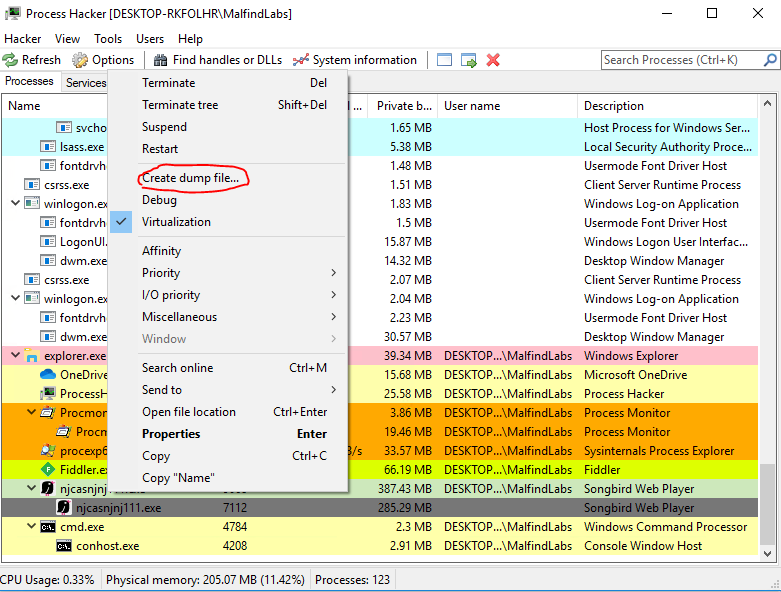
Once we dump a memory of the correct process (not the suspended one), it will create a .dmp file on the disk. This file we can analyze this in multiple ways, but the easiest one will be to dump strings. For this, we will use a tool called FLOSS – also from Mandiant – which is like an improved version of a well known linux command “strings”.
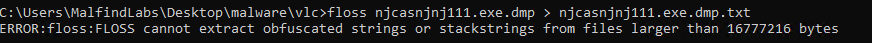
After running FLOSS we need to dump strings to some text files. It will create quite a big file with a lot of strings, so it will be difficult to read the mall one by one. But because strings are dumped by their proximity in memory regions, we can search for something we know malware uses, and then look from there. It is a much more effective method than simply trying to check all the strings. Here we will search for C2 IP, which will have multiple results, but after some time with some scrolling and luck, we can find some interesting strings.
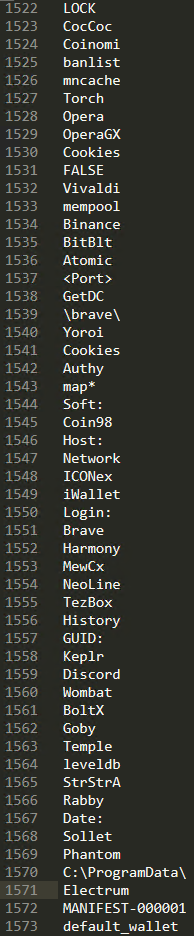
This looks interesting. Based on what we already know, this looks like a list of targets for Vidar. Especially it seems to target cryptocurrency wallets, internet browsers’ cookies, and password files. This is indeed consistent with Vidar writeups we can find online. With more time we can find even more interesting strings.
That’s about it for this quick blog post. There is much more we can do with this sample, including deep dive into its capabilities with specialized revere engineering tools, but the goal of this article was to give you very basic capabilities to be able to triage every malware in 30 minutes. As you can see this is still very powerful. I hope you learned something from this post.
Indicators of compromise:
SHA-256 Hashes:
582C4ACBC092B21873D8783FD598434D4699FFD5727C193565CF6A123BF34D28 4e70000.njcasnjnj111.exe 77648473A36693CE3547880CB361F10ED937F0D43839CAD51DE7C8D4AC9709B8 njcasnjnj111.exe 9CB1F2B183CA9D483D6FCA28A307D39EF9BE3A802CFC6C94E543C62E8DEBD67C Setup.exe B43BD295397F315BC897900FF892BBB9EAFD4E4B5D608443451E37D554934C0E SoftwareSetupFile.zip
Network indicators:
hxxps://cdn.discordapp[.]com/attachments/1001817794473631826/1047719457142865950/njcasnjnj111.exe hxxps://t[.]me/asifrazatg hxxps://steamcommunity[.]com/profiles/76561199439929669 hxxp://116.202.6[.]206/1711 hxxp://116.203.0[.]170:80 hxxp://88.198.77[.]204
Samples links:
https://www.virustotal.com/gui/file/77648473a36693ce3547880cb361f10ed937f0d43839cad51de7c8d4ac9709b8 https://www.virustotal.com/gui/file/9cb1f2b183ca9d483d6fca28a307d39ef9be3a802cfc6c94e543c62e8debd67c https://www.virustotal.com/gui/file/582c4acbc092b21873d8783fd598434d4699ffd5727c193565cf6a123bf34d28 https://analyze.intezer.com/analyses/3fc524e4-11e4-4e2a-9e95-d84fc3d3b573/sub/2a654839-10ab-4a99-a541-9d427914a8b0/string-reuse https://tria.ge/221201-gktv1adh3v